Install OpenLDAP and LDAP Account Manager on debian
Introduction
LDAP (Lightweight Directory Access Protocol) is a network protocol that enables to query user directories.
It is widespread in computer systems, and there exists several implementations.
OpenLDAP is an opensource implementation of the LDAP protocol that can be easily installed on a Linux sytem.
While OpenLDAP can be managed via some command lines, there exist some tools that enable to manage OpenLDAP with a user-friendly web interface, such as LDAP Account Manager .
In this article we will cover the installation of OpenLDAP and LDAP Account Manager on a debian host.
The configured LDAP will handle users and groups for the domain jonathanpastor.fr.
OpenLDAP
Installation of OpenLDAP on debian
First, let's refresh the package list and install slapd and ldap-utils
During the installation, you will be asked to choose an administration password for the admin account:
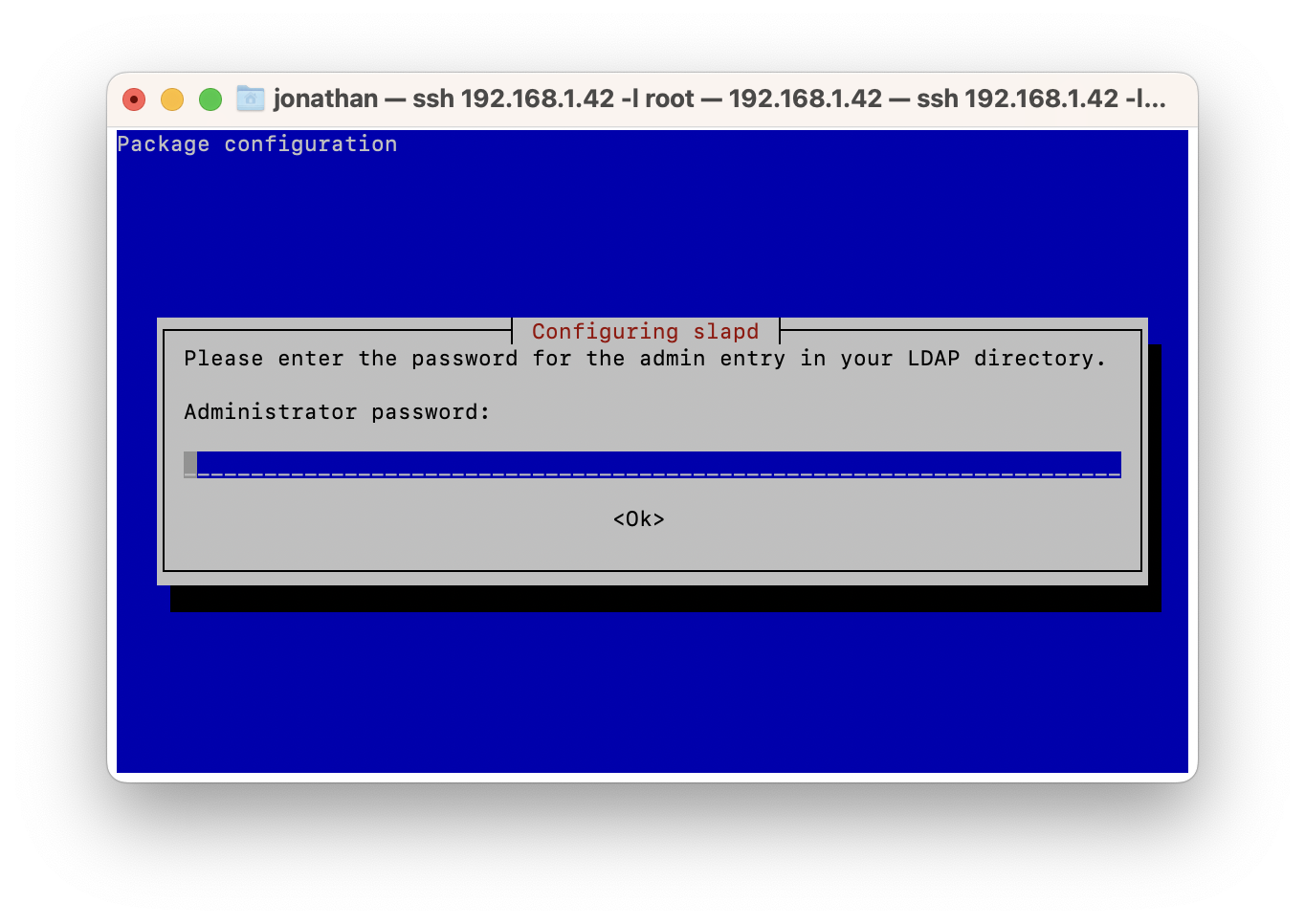
Configuring OpenLDAP
Now we will initialize a group and a user in OpenLDAP.
First we create the basis for the domain. Create a file named basedn.ldif with the following content
dn: ou=people,dc=jonathanpastor,dc=fr
objectClass: organizationalUnit
ou: people
dn: ou=groups,dc=jonathanpastor,dc=fr
objectClass: organizationalUnit
ou: groups
And execute the following command:
If it worked, you should get a similar output:
adding new entry "ou=people,dc=jonathanpastor,dc=fr"
adding new entry "ou=groups,dc=jonathanpastor,dc=fr"
LDAP Account Manager
Installation of LDAP Account Manager
First, we will install dependencies for LDAP Account Manager:
apt install -y libapache2-mod-php php php-fpm php-ldap php-gd php-imagick php-curl php-zip php-xml php-gmp php-mbstring gettext fonts-dejavu ckeditor libjs-jquery-jstree
Go to the download page of LDAP Account Manager, and download the version that corresponds to your operating system. In our case, we will use the debian version :
wget https://github.com/LDAPAccountManager/lam/releases/download/8.5/ldap-account-manager_8.5-1_all.deb?download -O ldap_account_manager.deb
Now, install LDAP Account Manager:
LDAP Account Manager should be accessible on the port 80 at "http://$IP_ADDRESS/lam" via a Web browser:
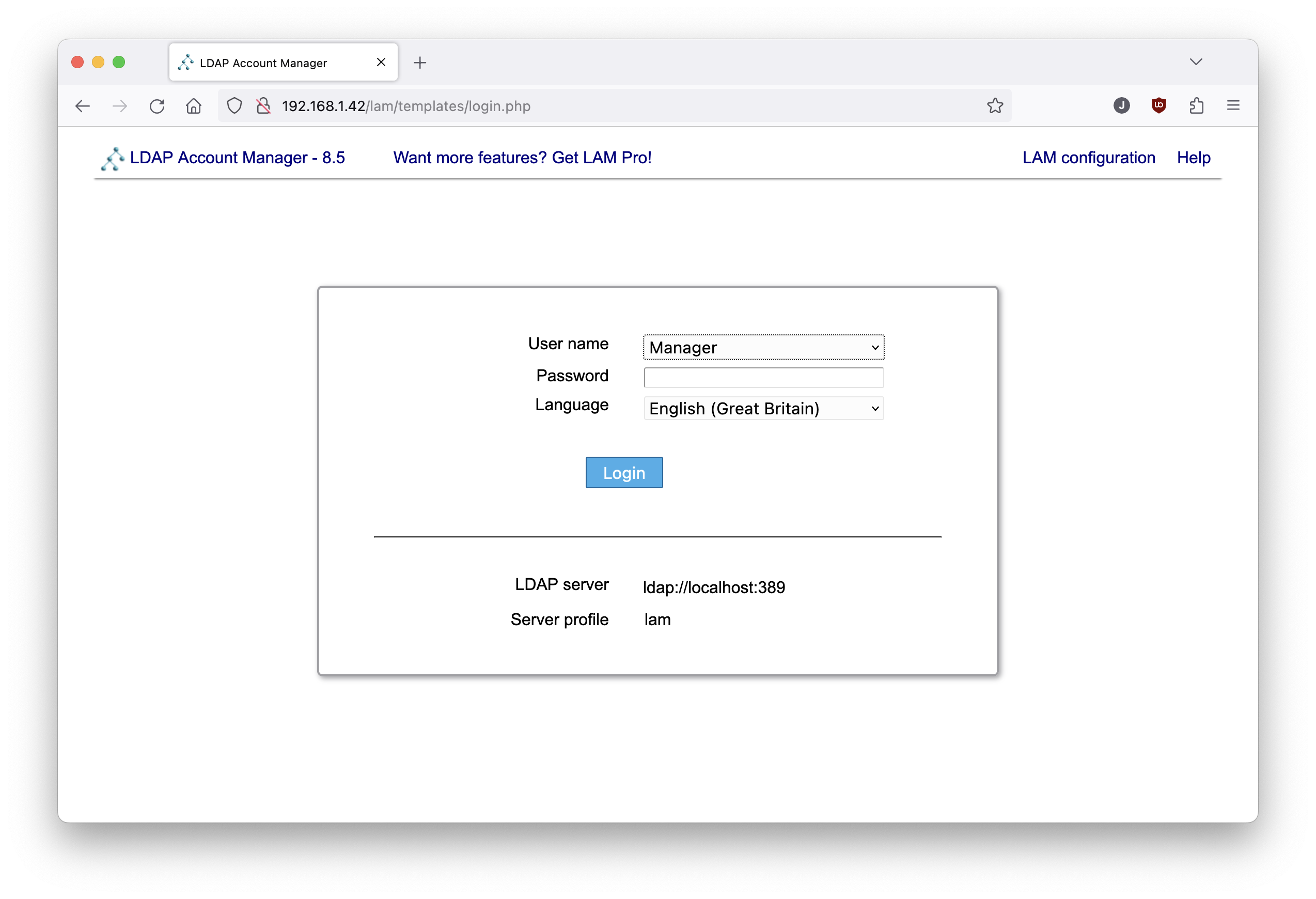
Configuration of LDAP Account Manager
Most of the configuration will be done in the server profile editor, located at http://$IPADDRESS/lam/templates/config/conflogin.php .
To access this editor you have to use the lam account preconfigured with lam as password.
Configuration of the domain and default admin in LDAP Account Manager
First, edit the following screens:
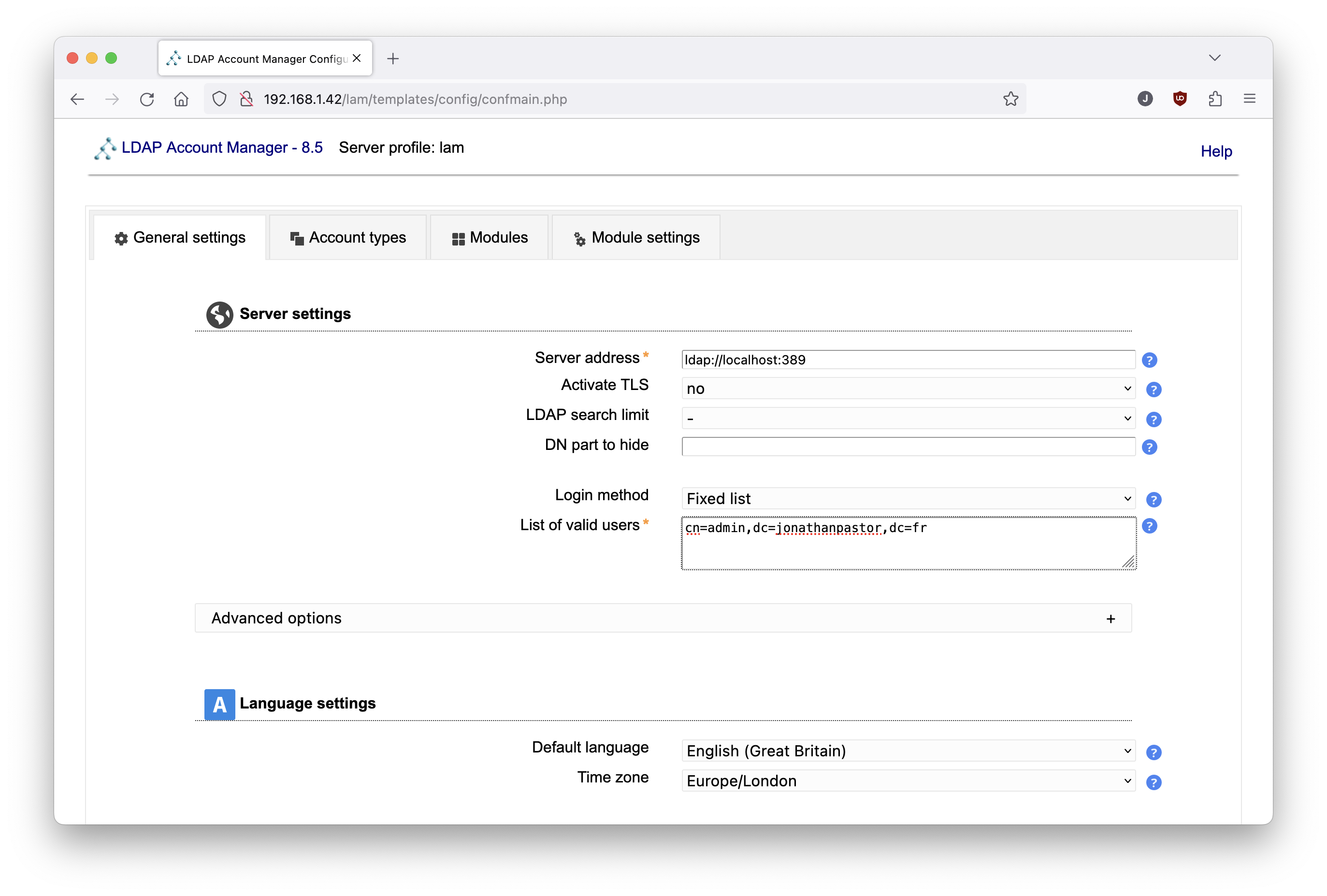
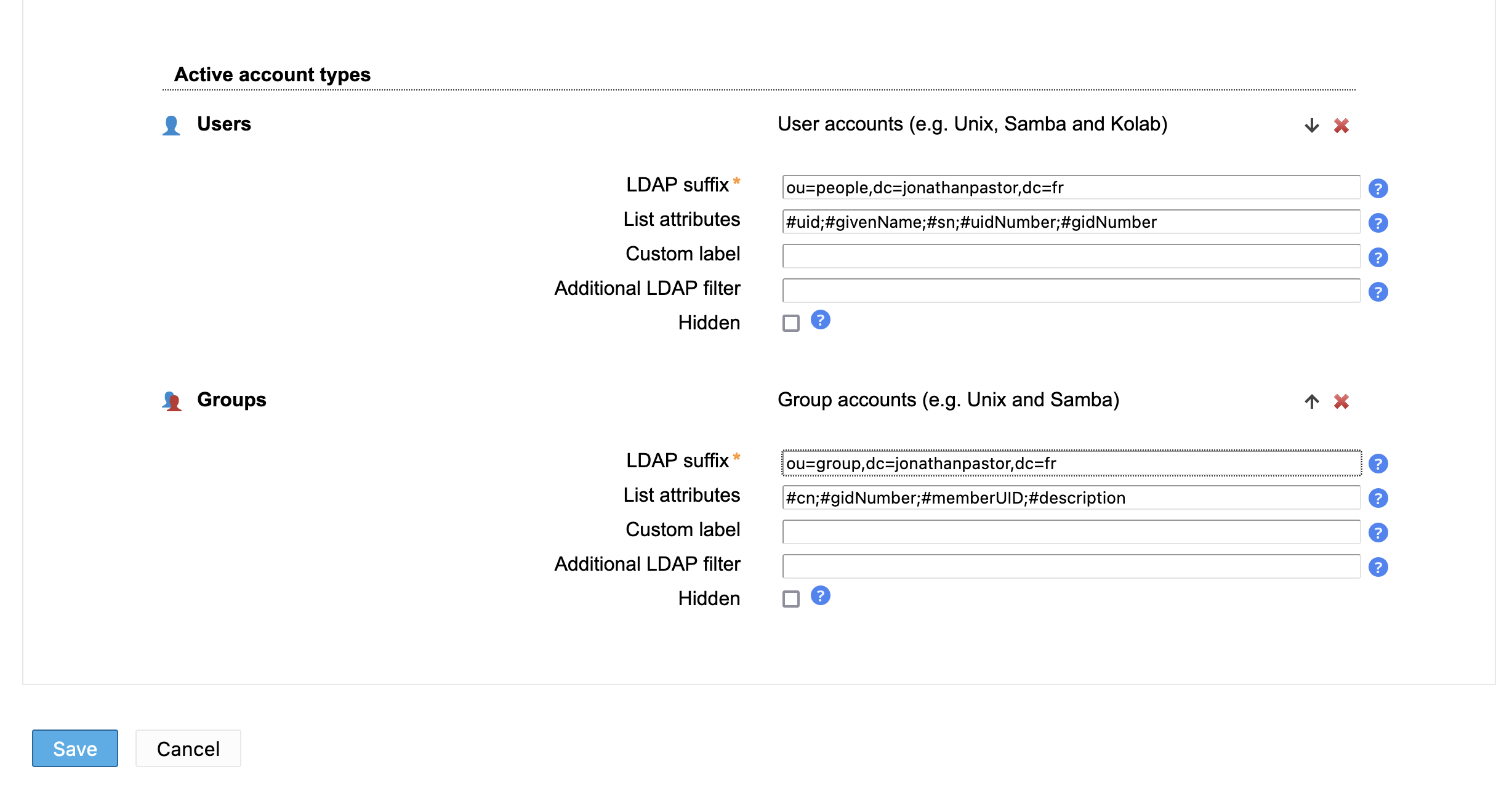
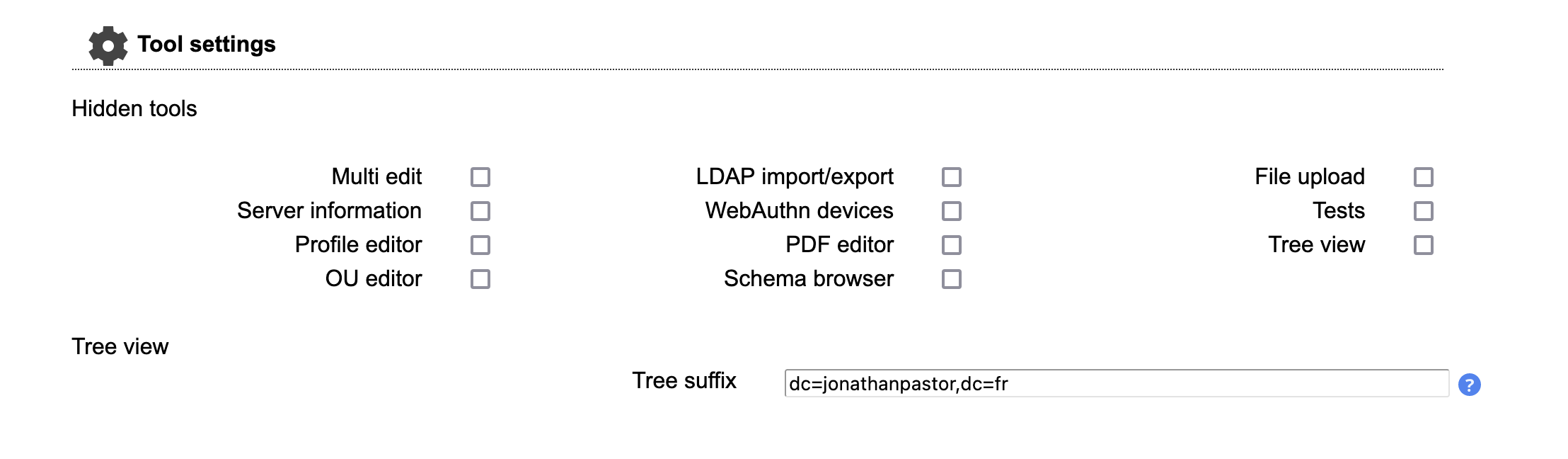
Don't forget to persist your changes by clicking on the save button in the bottom of the configuration page!
Now, you should be able to log in to the LDAP Account Manager using the admin user.
Creation of a Unix Group, an organizational Unit and a first User
Now log with the admin account using the password chosen during the install of OpenLDAP.
LDAP Account manager should ask to create a group, as in the following screenshot.
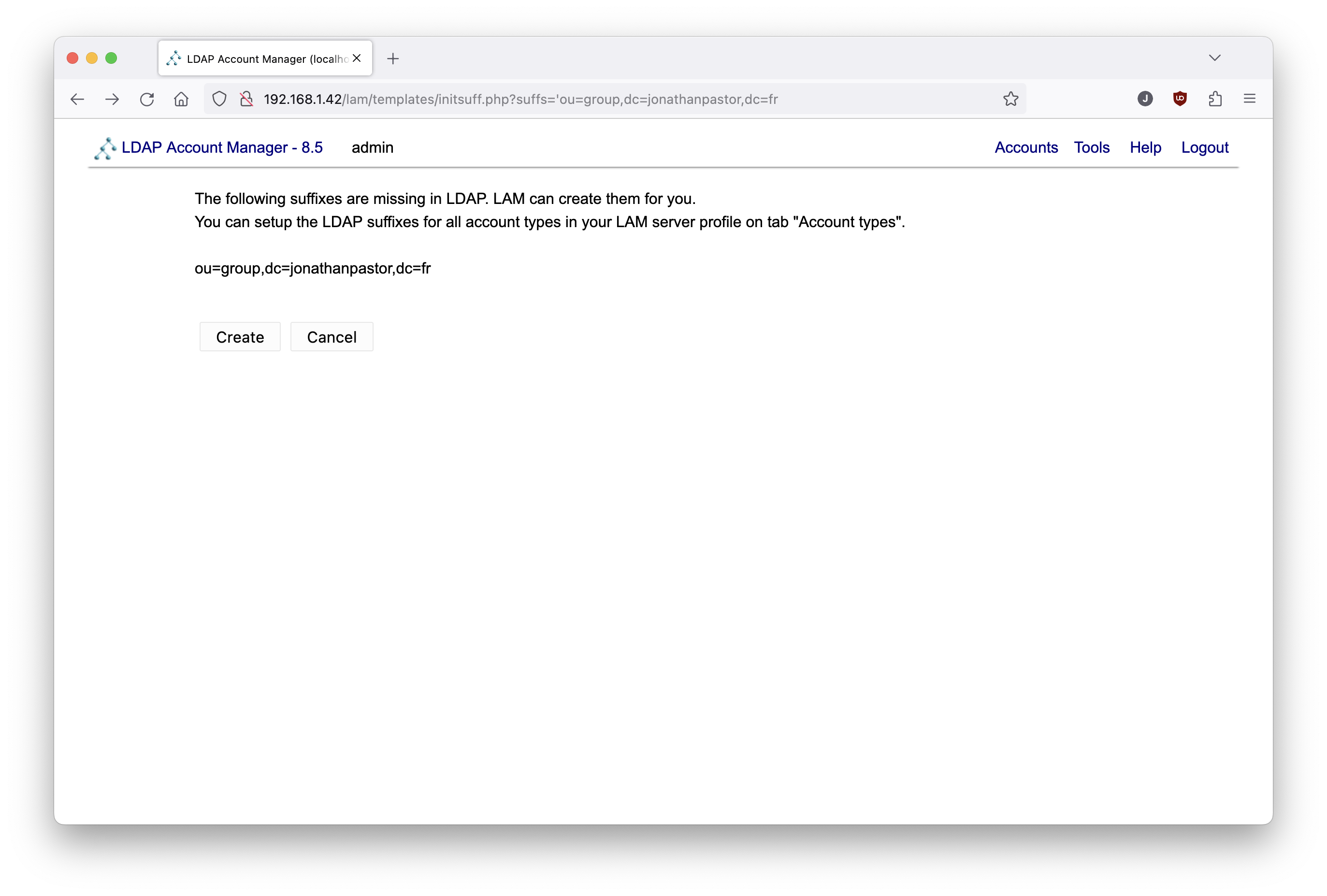
Accept to create the organizational unit by clicking on the create button.
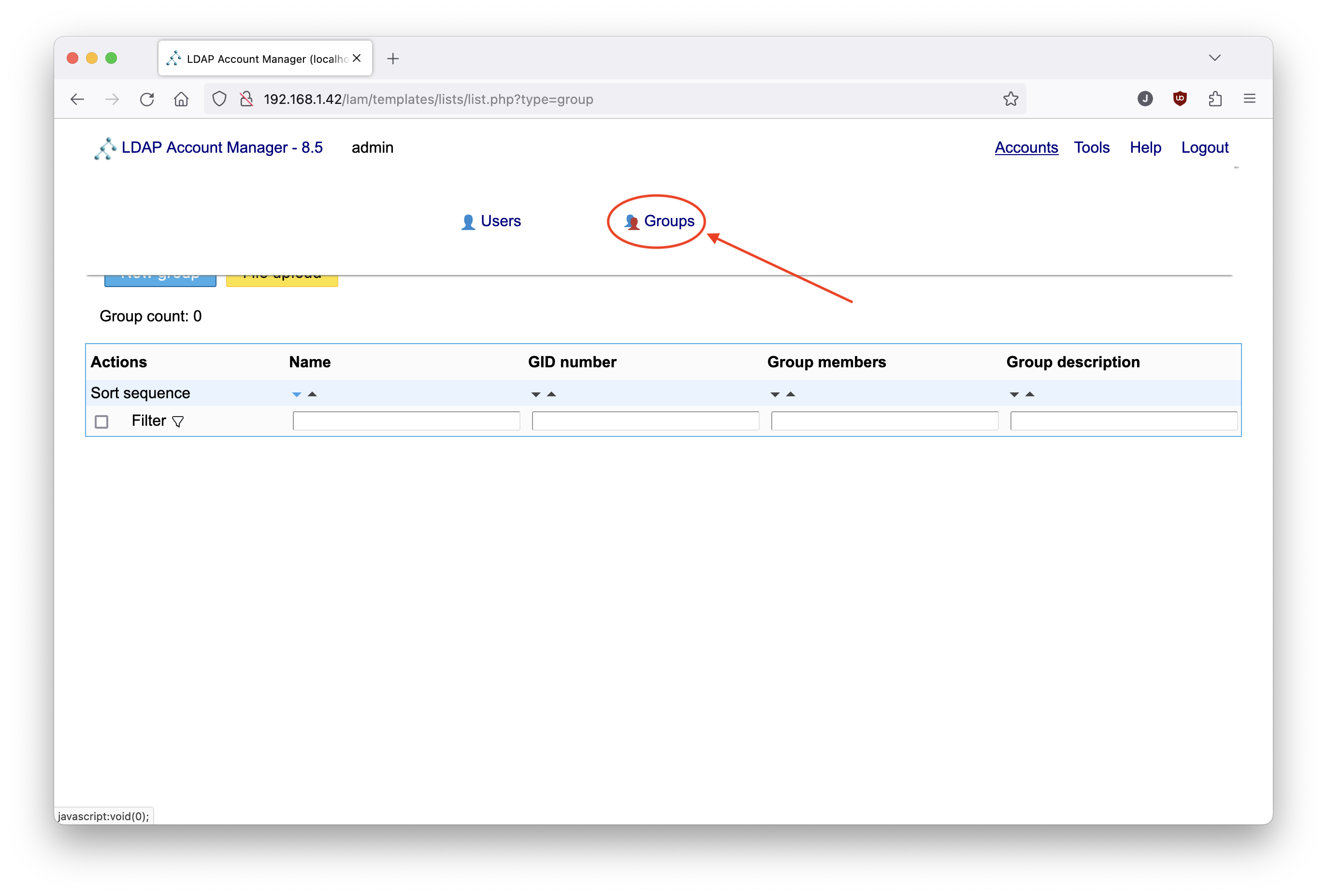
The first thing that we will do is to create a unix group that will be used by LDAP Account Manager to register the new users. First move the mouse cursor in the top of the web page, and click on Groups to access the interface where you can manage groups:
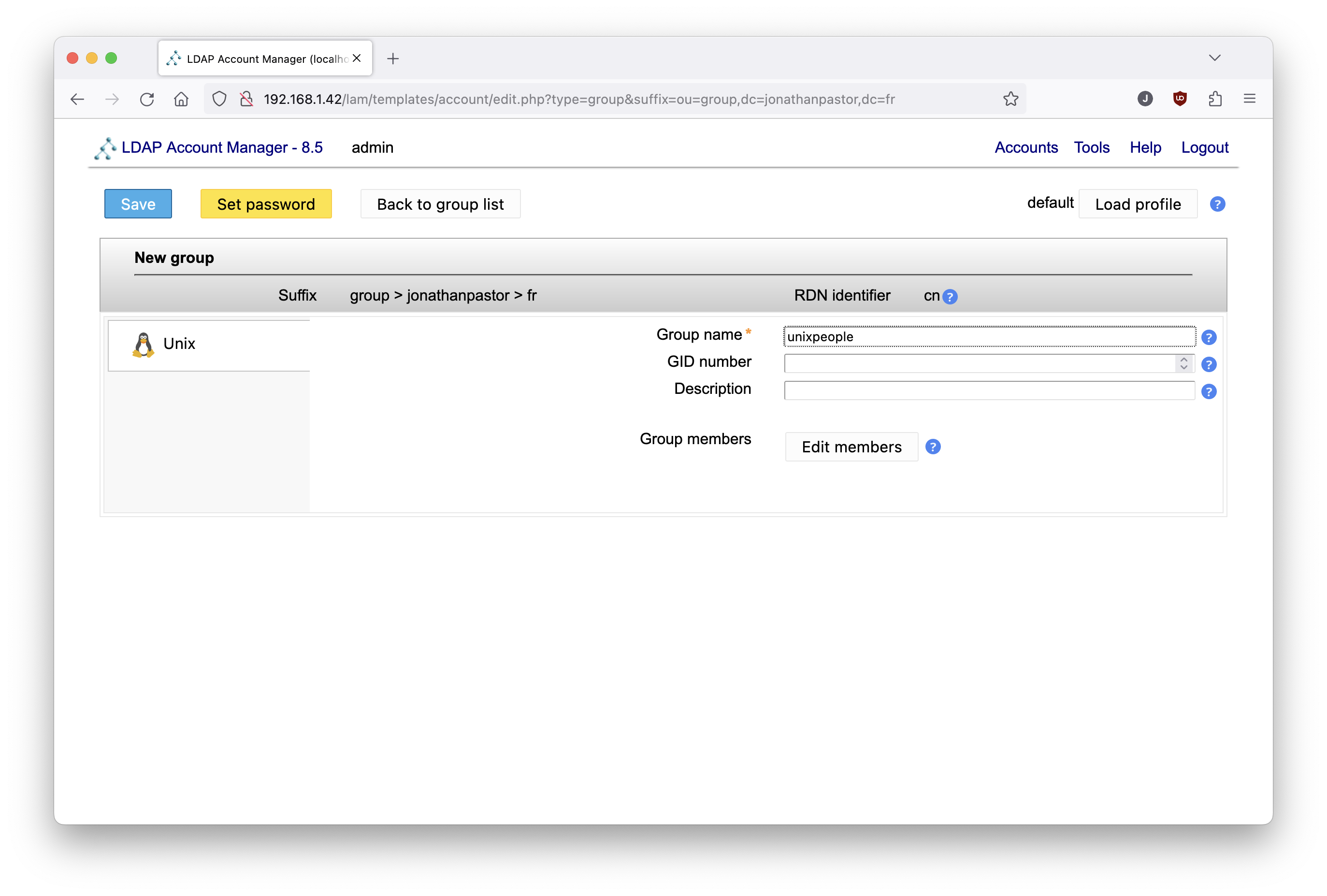
Click on the new group button, and create a unix group with the name of your choice:
Add an organizational unit for admins (dc=admins,dc=people,dc=jonathanpastor,dc=fr)
We will now create an organizational unit for users that will later receive administrative privileges.
Move the cursor over the Tools text in the top right corner of the webpage, then select Tree View:
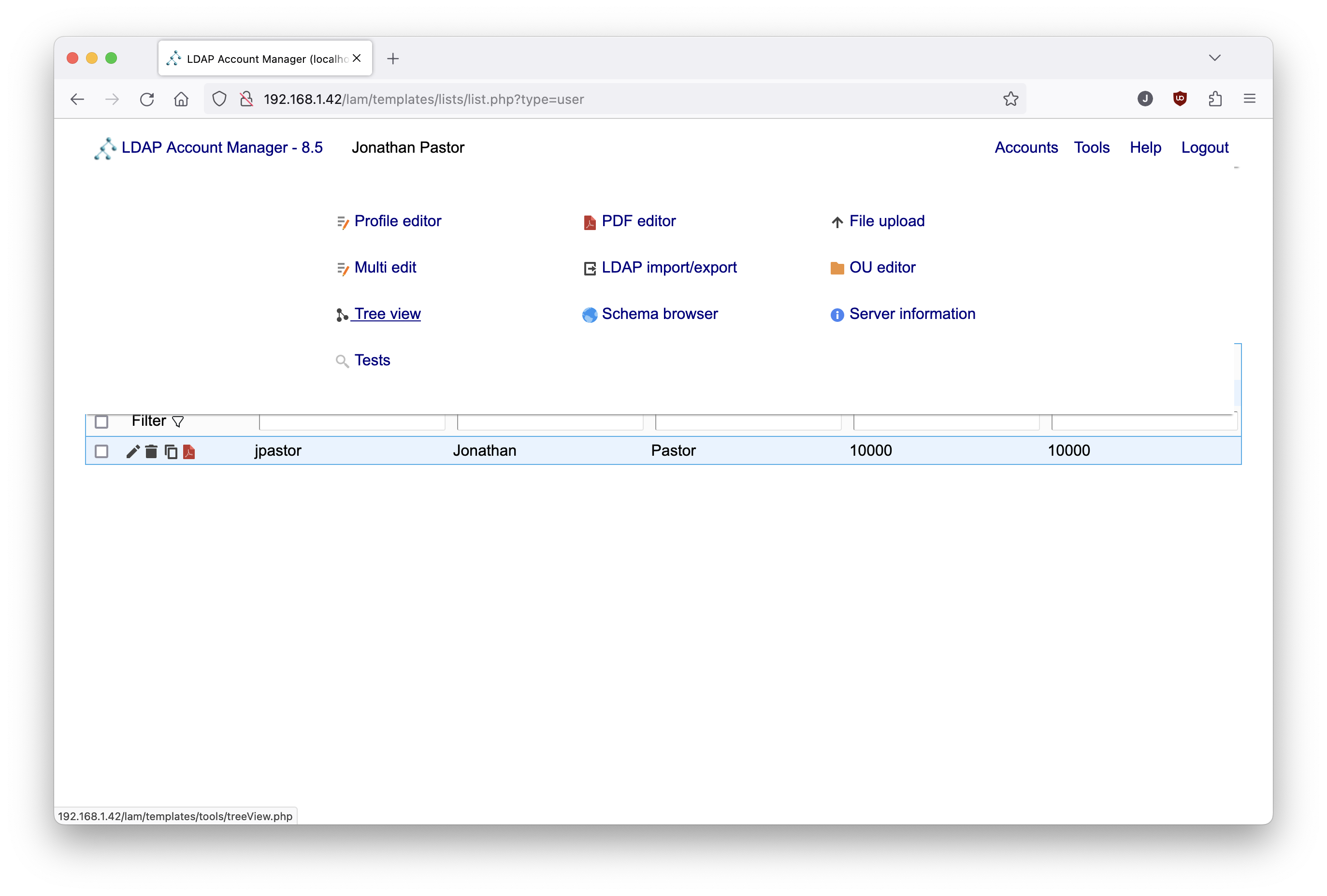
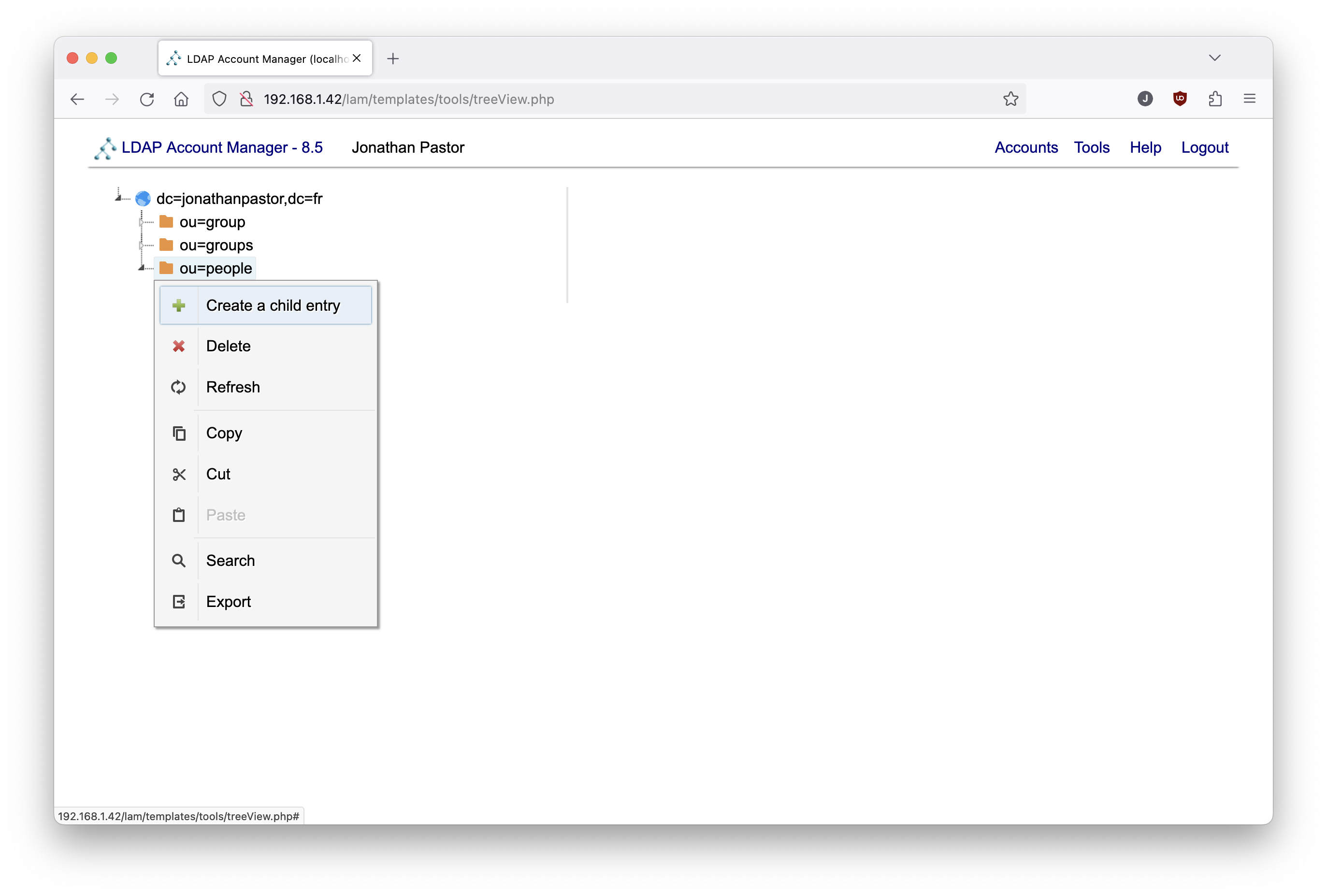
Then right-click on the node corresponding to the "people" organizational unit, and select the Create a child entry.
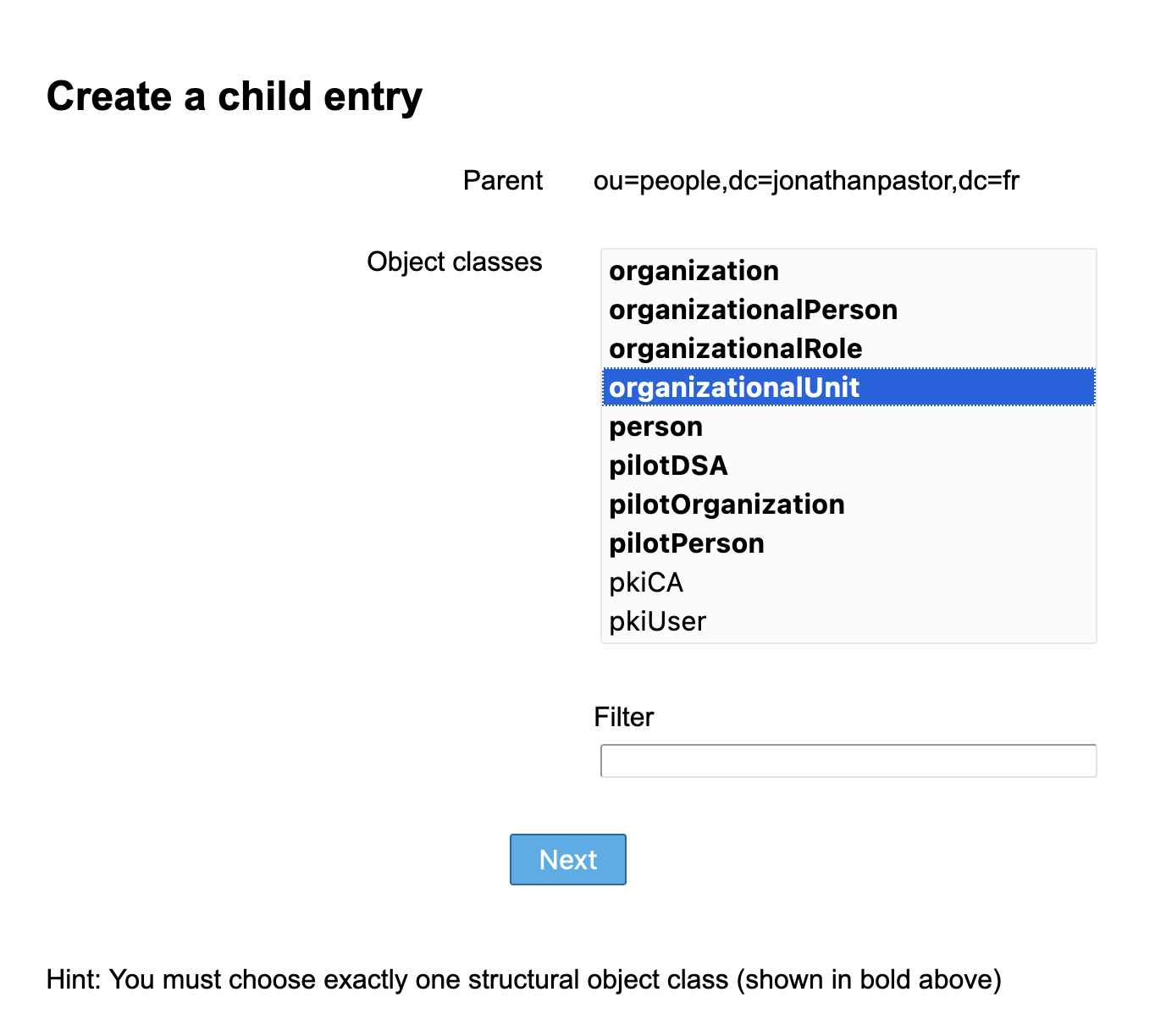
Then select organizationalUnit as object class and click on next:
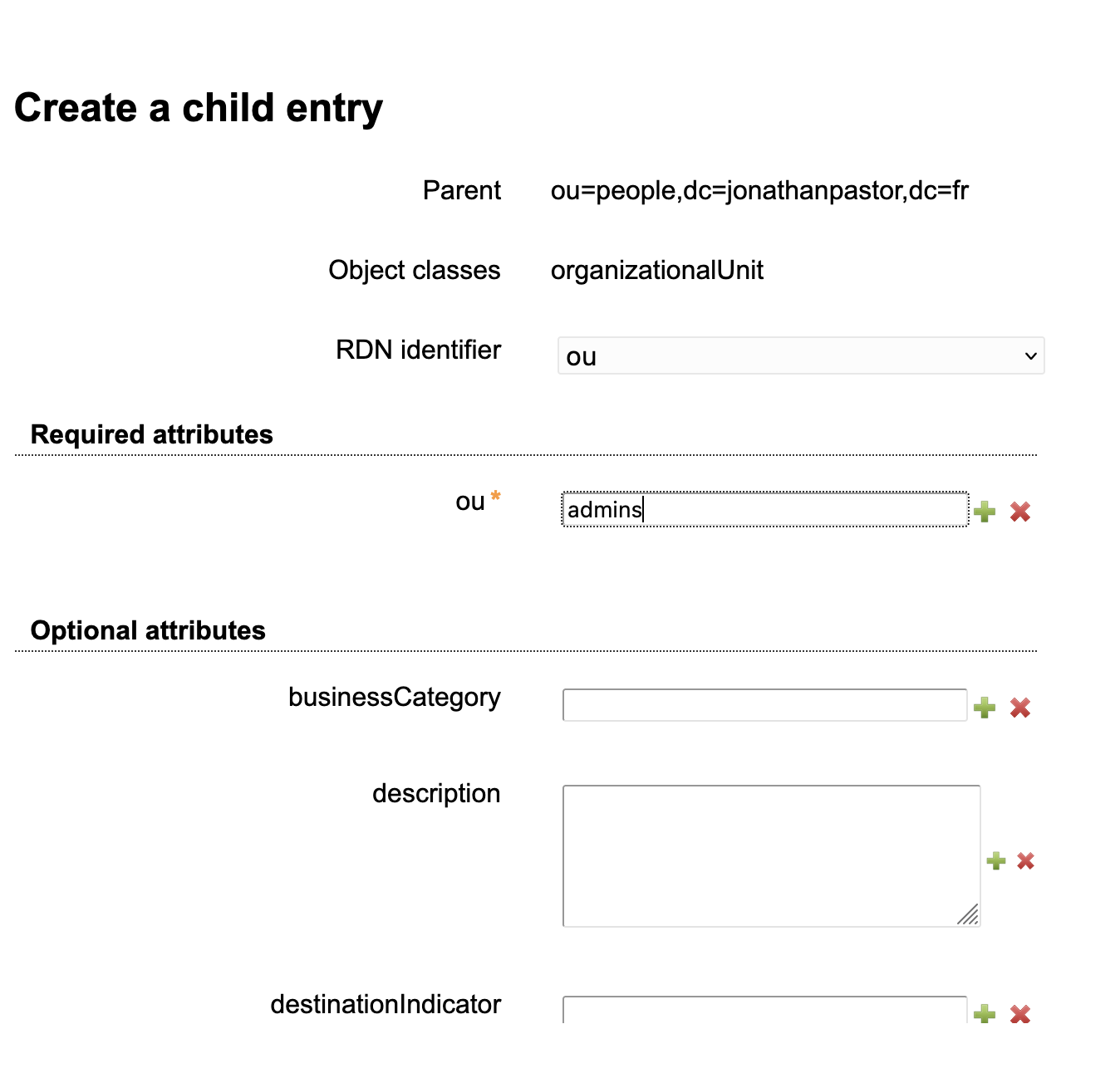
And call this class admins:
Create a user in dc=admins,dc=people,dc=jonathanpastor,dc=fr
We will now create a user in the admins organization unit.
Move the cursor over the Accouts text in the top right corner of the webpage, then select Users:
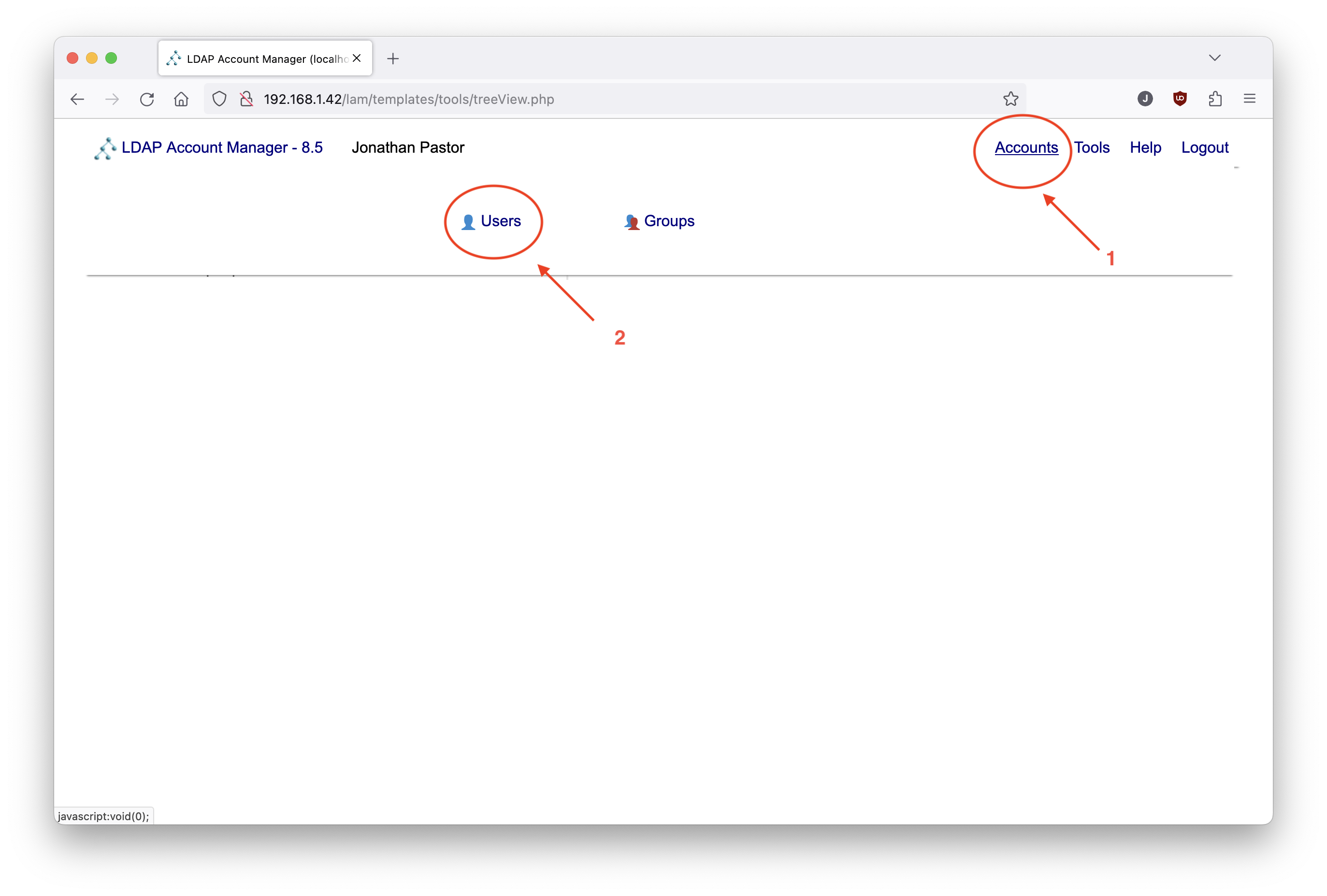
Click on the New user button:
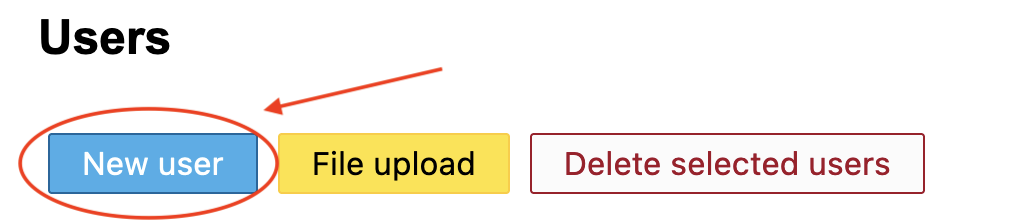
Enter some values for the first name and lastname:
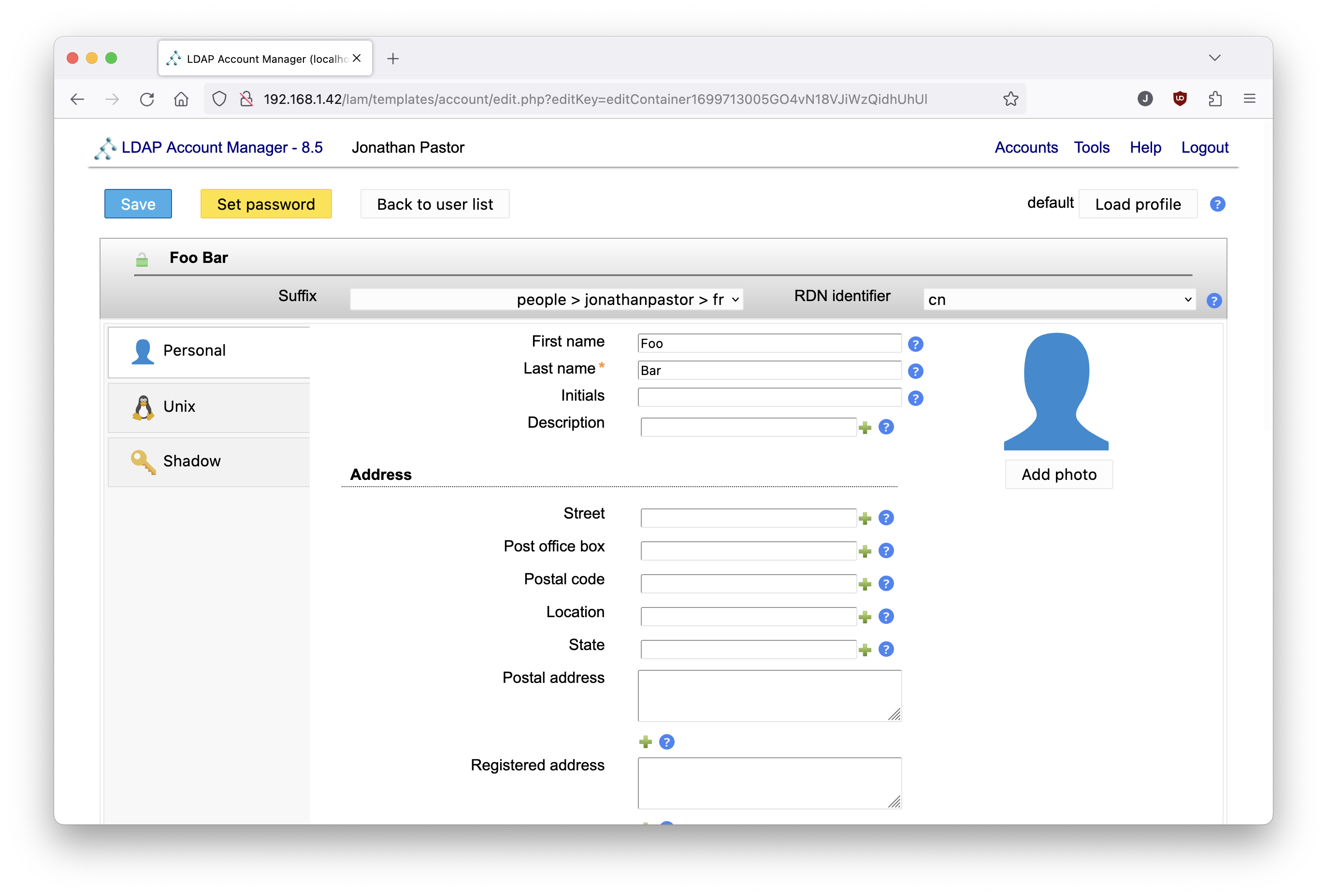
Ensure that data in the unix part is correct:
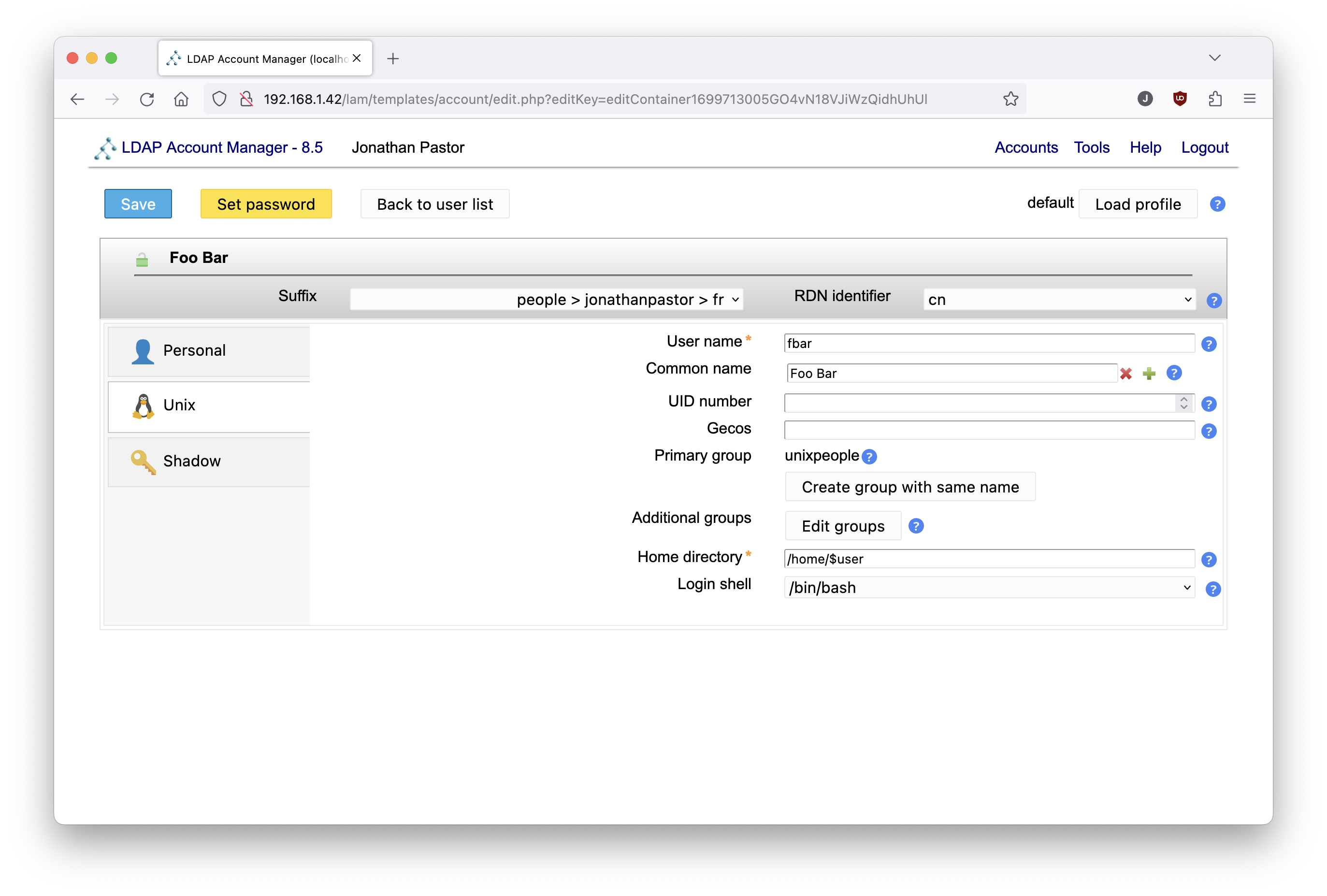
Ensure that the new user will be in the admins organizational unit:
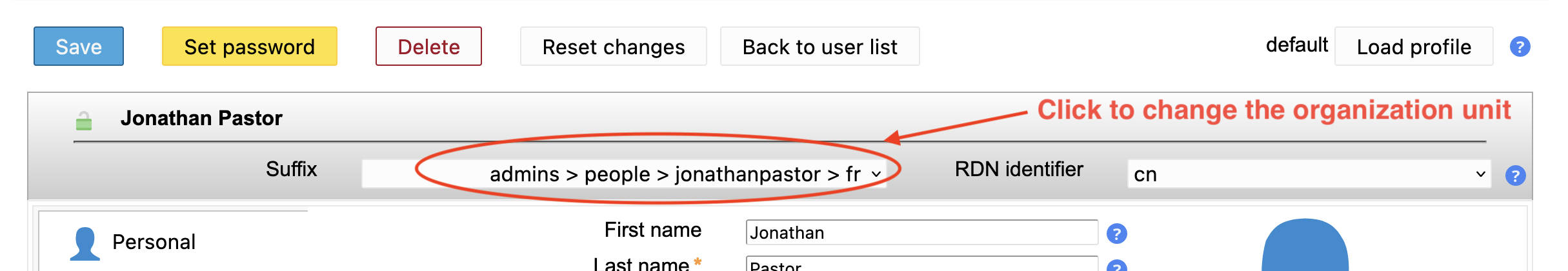
Define a password and then save the user:
Enabling modifications by members of dc=admins,dc=people,dc=jonathanpastor,dc=fr
Create a file ACL.ldif with the following content:
dn: olcDatabase={0}config,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external
,cn=auth manage by * break
olcAccess: {1}to * by * read
dn: olcDatabase={1}mdb,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to attrs=userPassword
by self write
by anonymous auth
by dn.subtree="ou=admins,ou=people,dc=jonathanpastor,dc=fr" write
by * break
olcAccess: {1}to attrs=shadowLastChange by self write by * read
olcAccess: {2}to *
by dn.subtree="ou=admins,ou=people,dc=jonathanpastor,dc=fr" write
by * read
And import the file via the following command:
Only admins can connect to LDAP Account Manager
Go to the LAM server profile editor, and edit
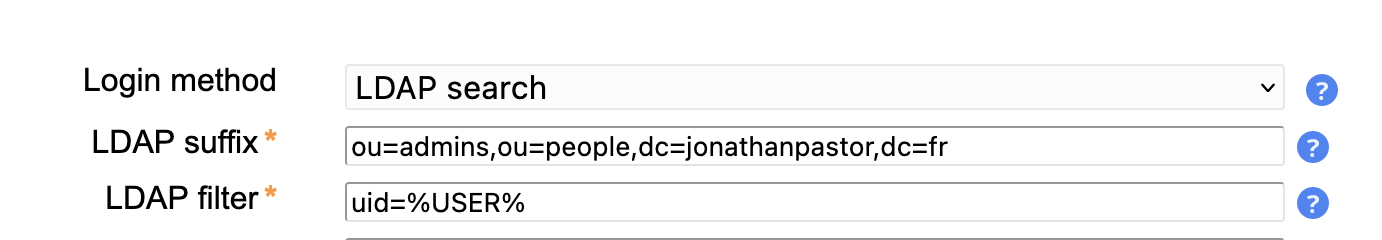
In the LDAM server profile editor, change the Login method to LDAP search and use these values:
- LDAP suffix:
ou=admins,ou=people,dc=jonathanpastor,dc=fr - LDAP filter:
uid=%USER%
as in the following screenshot:
Using the LDAP Account Manager
With the configuration made in the previous sections,
all members of the admins organizational unit can create and modify users of the LDAP.
The LDAP is also fully operational and can be integrated in third party tools.
References
To sucessfully set up OpenLDAP and LDAP Account Manager, I used several sources as inspiration:
- http://docs.switzernet.com/3/public/101010-ldap/
- https://wiki.debian.org/LDAP/OpenLDAPSetup#Permissions
- https://www.howtoforge.com/how-to-install-openldap-on-debian-11/